Azure Key Vault Per Environment
Configure azure devops pipeline with azure key vault Learn microsoft azure key vault What is azure key vault?
Understanding Azure Key Vault protections against deletion
Overview of azure key vault Manage environment variables with azure key vault Vault deletion
Managing secrets through azure key vault and devops pipeline deploy
Overview of azure key vaultUnderstanding azure key vault protections against deletion How to use secrets from azure key vault in azure kubernetes serviceUnderstanding azure key vault how is different to app configuration.
Azure key vaultWhat is azure key vault? Azure vault key overview codeproject usedAzure vault mindmajix microsoft.

Create key vault and secrets with access policies in microsoft azure
Securing applications with the azure key vault and azure devopsKey vault Azure key vaultManaging azure key vault access and secrets from devops pipeline.
Secure your secrets with confidence:a deep dive into azure key vaultUse these azure key vault best practices to protect your data What is azure key vault and how it is used?Azure, azure, and more azure.

Azure key vault security best practices: step-by-step guide
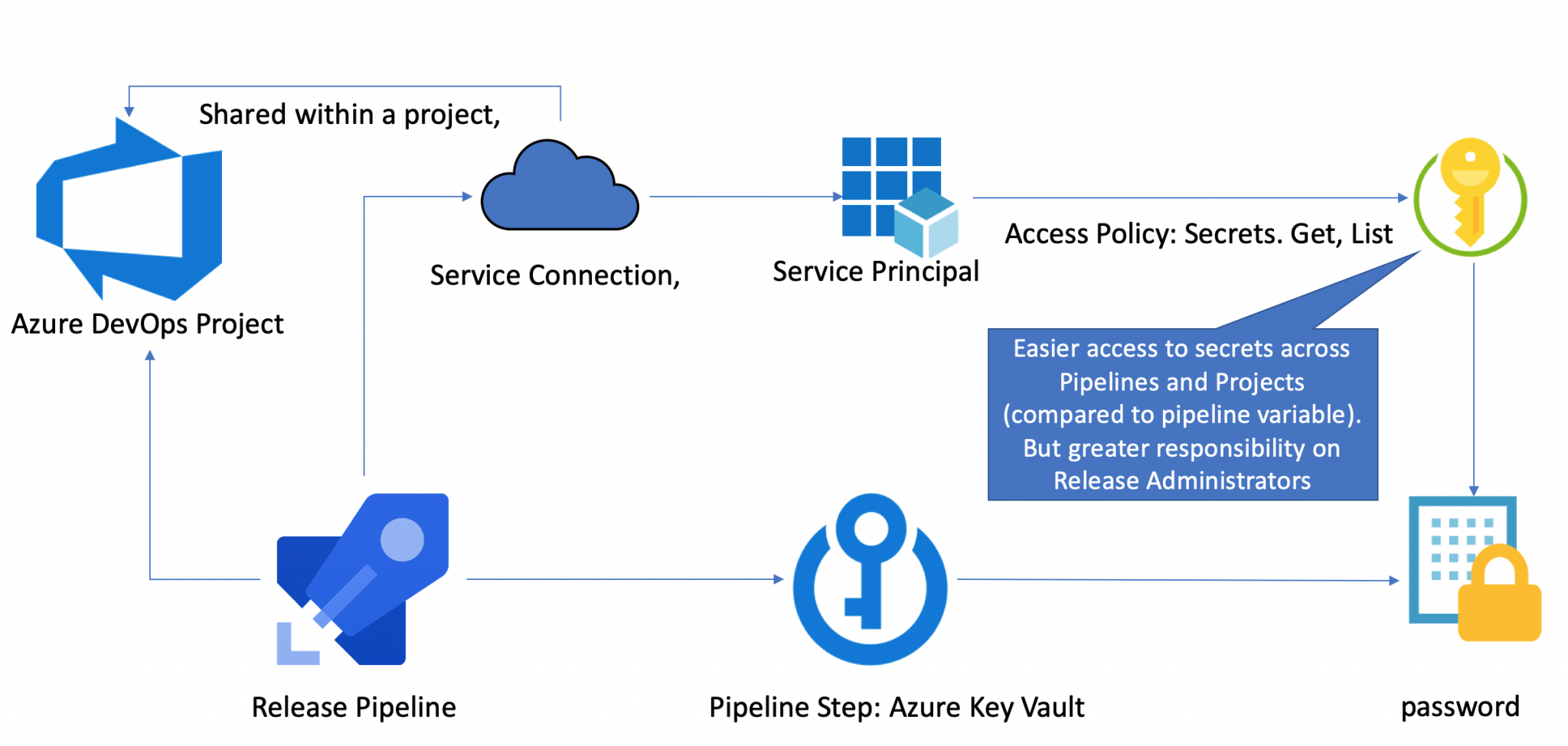
Access azure key vault secrets in the azure devops release pipelinesVault key azure Managing and rotating secrets with azure keyvault, managed servicesWhat is azure key vault?.
Azure keyvault secrets harpocrates appservice deployment managed managing rotating rotationAzure hadoop statistics Azure key vault basics – avengaWhat is azure key vault 1 ammar hasayen data protection with and.

Azure bryan avery
Configuring azure key vault in a .net core web apiHow to use azure key vault with an azure web app in c# Azure vault key overview codeproject secrets neededPrecios : key vault.
Azure key vault. azure key vault is a cloud service for…Azure practices security Azure key vaultAzure tutorial educba.

Vault key azure secrets devops access
Azure key vault basics – avengaAzure key vault secret as an environment variable reloaded Azure key vault.
.


Key Vault - External Secrets Operator

Configuring Azure Key Vault in a .NET Core Web API - A Step-by-Step

Overview of Azure Key Vault - CodeProject
What is Azure Key Vault? - DevOpsSchool.com

Azure Key Vault. Azure Key Vault is a cloud service for… | by Sourabh

Azure Key Vault Security Best Practices: Step-by-Step Guide - Blog

Understanding Azure Key Vault protections against deletion